Hacker group targeting crypto executives with AI-driven tools, warns Kaspersky

Kaspersky’s Global Research and Analysis Team (GReAT) revealed the latest BlueNoroff APT activity through two highly targeted malicious campaigns, ‘GhostCall’ and ‘GhostHire’. The ongoing operations have targeted Web3 and cryptocurrency organizations across India, Turkey, Australia, and other countries in Europe and Asia since at least April 2025. The announcement was made at the Security Analyst Summit in Thailand, of which MENA TECH is the exclusive Middle East media partner.
BlueNoroff, a branch of the notorious Lazarus group, continues to expand its signature ‘SnatchCrypto’ campaign, a financially driven operation targeting the global crypto industry. The newly revealed GhostCall and GhostHire campaigns use new infiltration methods and customized malware to compromise blockchain developers and executives. These attacks mainly target macOS and Windows systems and are managed through a centralized command-and-control infrastructure.
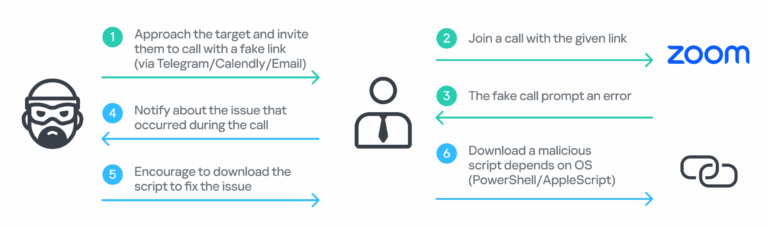
The GhostCall campaign targets macOS devices, beginning with a highly sophisticated, personalized social engineering attack. The attackers contact victims through Telegram, impersonating venture capitalists and sometimes using compromised accounts of real entrepreneurs and startup founders to promote investment or partnership opportunities. The victims are invited to fake investment meetings on phishing sites that mimic Zoom or Microsoft Teams, during which they are prompted to “update” their client to resolve an audio issue. This action downloads a malicious script and installs malware on the device.
“This campaign relied on deliberate and carefully planned deception. Attackers replayed videos of previous victims during staged meetings to make the interaction appear like a real call and manipulate new targets. The data collected in this process is then used not only against the initial victim but also exploited to enable subsequent and supply-chain attacks, leveraging established trust relationships to compromise a broader range of organizations and users,” comments Sojun Ryu, security researcher at Kaspersky GReAT.
Attackers used seven multi-stage execution chains, four of which were previously unseen, to distribute a variety of new customized payloads, including crypto stealers, browser credential stealers, secrets stealers, and Telegram credential stealers.
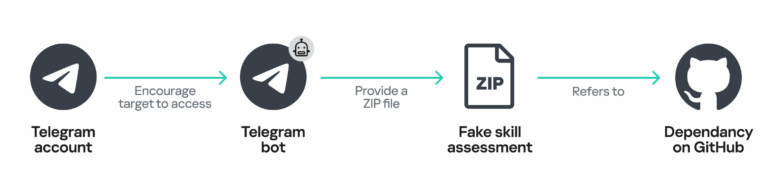
In the GhostHire campaign, the APT targets blockchain developers by posing as recruiters. Victims are deceived into downloading and executing a GitHub repository containing malware, presented as a skill assessment. GhostHire shares its infrastructure and tools with the GhostCall campaign, but instead of using video calls, it focuses on approaching hands-on developers and engineers through fake recruitment efforts. After initial contact, victims are added to a Telegram bot that delivers either a ZIP file or a GitHub link, along with a short deadline to complete the task. Once run, the malware installs itself on the victim’s machine, tailored for the operating system.
The use of generative AI has enabled BlueNoroff to accelerate malware development and refine its attack methods. The attackers introduced new programming languages and added extra features, making detection and analysis harder. It also helps the actor manage and grow its operations, increasing both the complexity and extent of attacks.
“Since its previous campaigns, the threat actor’s targeting strategy has evolved beyond simple cryptocurrency and browser credential theft. The use of generative AI has significantly accelerated this process, enabling easier malware development with reduced operational overhead. This AI-driven approach helps to fill the gaps in available information, enabling more focused targeting. By combining compromised data with AI’s analytical capabilities, the scope of these attacks has expanded. We hope our research will contribute to preventing further harm,” comments Omar Amin, senior security researcher at Kaspersky GReAT.
More information, together with the indicators of compromise, is available in a report on Securelist.com.
To stay protected from attacks such as GhostCall and GhostHire, organizations are advised to follow these best practices:
- Be cautious with generous offers and investment proposals. Verify the identity of every new contact, especially those reaching out via Telegram, LinkedIn, or other social platforms. Use verified and secure corporate channels for all sensitive communications.
- Consider the possibility that a trusted contact’s account might be compromised. Confirm identities through alternative channels before opening any files or links, always ensuring you’re on an official domain. Do not run unverified scripts or commands to fix issues.
- To safeguard the company against various threats, utilize solutions from the Kaspersky Next product line that offer real-time protection, threat visibility, and the investigation and response capabilities of EDR and XDR for organizations of any size and industry. Based on your current needs and available resources, you can select the most appropriate product tier and easily upgrade to another as your cybersecurity requirements evolve.
- Adopt managed security services covering the entire incident management cycle – from threat identification to continuous protection and remediation. They help protect against evasive cyberattacks, investigate incidents, and provide additional expertise, even when a company lacks cybersecurity workers.
- Give your InfoSec professionals comprehensive visibility into cyber threats targeting your organization. The latest Kaspersky Threat Intelligence offers detailed and relevant context throughout the entire incident management cycle, helping them identify cyber risks promptly.






































